Security researchers at CloudSEK have noticed an increase in the use of reverse tunnel service and URL shorteners in phishing campaigns. Cyber criminals use services such as bit.ly, Ngrok or LocalhostRun to evade detection and “launch untraceable phishing campaigns” according to the researchers.
Phishing campaigns may impersonate legitimate websites and services to steal user data such as passwords or credit card numbers. These may be hosted on registered domains, free web hosting services or hacked websites; all of these options have in common that takedowns are quick and easy, as it is usually enough to contact the hosting provider or registrar to do so. Most hosting providers offer direct contact options for abuse cases.
Hosting providers are required to cooperate with law enforcement and take down domains and webpages that are being used in phishing campaigns. Internet users may report phishing websites and pages to hosting providers as well.
URL shorteners, services that point one web address to another, have been used in the past in phishing campaigns. These services are used for legitimate purposes, such as turning long web addresses into shorter ones to better remember the addresses.
CloudSEK noticed an uptick in the use of URL shortening services and reverse tunnel services in phishing campaigns.
Reverse tunnel services are often used in local development environments, as they allow customers to access local computer systems on the Internet. Some Internet users use reverse tunnel services for other purposes, including the hosting of personal cloud services.
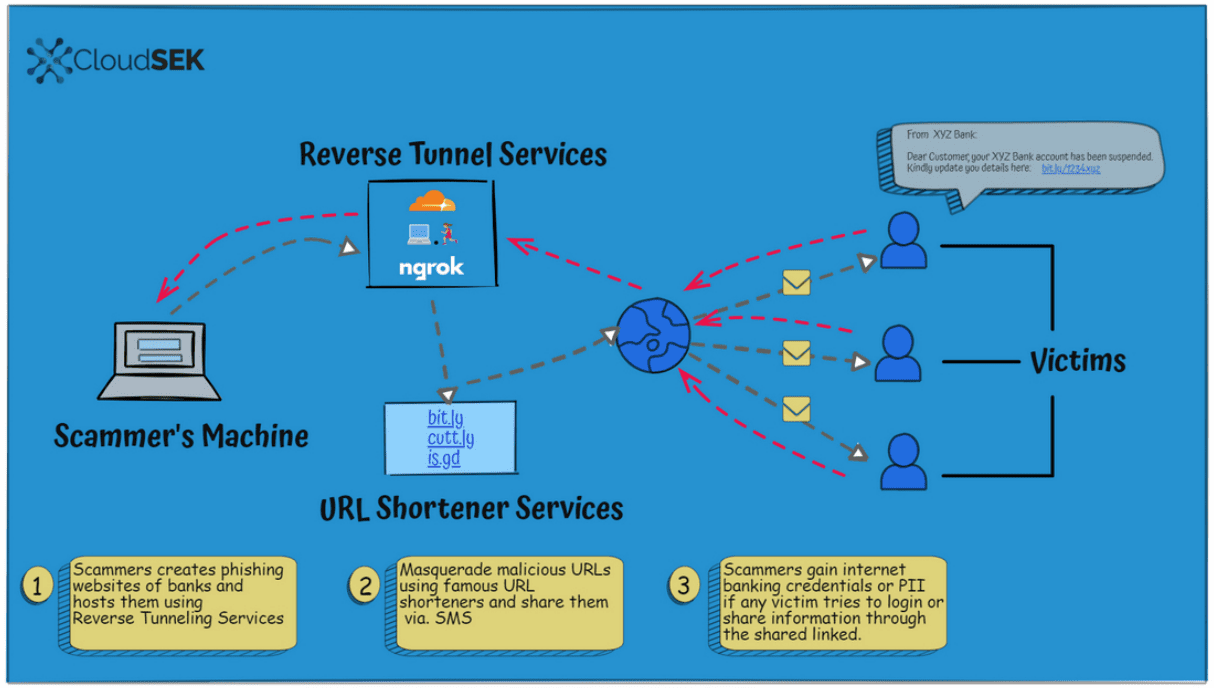
Cybercriminals use these services to host phishing pages on local machines. These local machines are under their control, either directly or through successful hacks. New redirect URLs can be generated on the fly, and it is easy enough to change the IP address of local machines to decrease the chance of attack interruptions caused by the blocking of IP address and domain names, or the taking down of webpages.
The combination of URL shortening services and reverse tunnel services obfuscates attacks even more. Links are often live for 24 hours only before the threat actors move on; this makes the blocking of campaigns that use these techniques difficult.
Local computer with phishing content >> Reverse Tunnel Service >> URL Shortening Service >> Attacks
Reserve tunnel operators don’t have the same level of accountability as hosting providers, according to CloudSEK. The company analyzed more than 500 sites that were “hosted and distributed using reverse tunnel services and URL shortening services Ngrok, LocalhostRun, Try CloudFlare, Bit.ly, is.gd, and cutt.ly.
The entire process begins with the creation of phishing websites and pages. These look like identical copies of legitimate sites, often banking sites and other financial sites, but other types of sites are used as well. The threat actors may host these on their own machines or on hacked devices.
Once the phishing pages and infrastructure has been created and is in place, reverse tunnel services come into play. These provide the link between the local machines and the Internet. URL shortening services are used to further obfuscate the campaign and make detection even harder.
The URL shortening links are then distributed in campaigns, e.g., by email, SMS, messaging services, or other means. Victims who access these links load the locally hosted webpages via the reverse tunnelling service’s URL.
Data that victims enter on the phishing websites is then captured and either used directly or sold on the black market. Attackers may clear out banking accounts, use credit cards for online purchases, including the registration of new domains and hosting, or sell information in bulk on the dark web.
Threat actors will refresh links regularly, often every 24 hours, to continue the attacks. Phishing templates are reused, as they are hosted on local machines and not on the Internet. All it takes is to create new random links using any of the listed services, or others, for use in new attacks. Links used in old attacks result in not found errors, as the local machines are no longer accessible through them.
While old pages and addresses may be blocked, for instance, when they are reported to security companies or the authorities, the phishing content can’t usually be taken down as it is hosted on local machines.
Cloudflare, Localhost, and Ngrok reverse tunnel services have in common that they provide links to webpages hosted on local machines.
Cloudflare’s Argo Tunnel service is free to use for Cloudflare users. It runs a process on the local machine or a server, that is creating outbound tunnels to the Cloudflare network. The Localhost and Ngrok reverse tunnel services offer a free base version and paid extended versions. Ngrok’s free plan, for instance, supports the use of random domains.
The service uses a secure reverse tunnel to “expose local servers behind NATs and firewalls to the public Internet”. A program is run on the local machine that establishes the link to the Internet.
All three services have in common that they are used by web developers and users alike to connect local machines to the Internet. Some may use reverse tunnel services to access personal cloud services from any location in the world, others to host websites or other services.
Mitigation
CloudSek recommends the following to mitigate phishing attacks that use reverse tunnel services:
- Organizations need to raise awareness among customers about legitimate domains and URLs; this applies to all types of phishing campaigns, as all host the phishing websites on different domains. While these may be made to look like authentic domains, inspection will show that they are not.
- Real-time scans may help identify phishing domains, especially if the scans look at more than just the domain name.
- Awareness needs to be raised among customers about malicious URLs and the use in phishing campaigns.
- Policies need to be implemented that “ensure reverse tunnel service providers” assist in the takedown of phishing sites.
The best form of protection against malicious attacks is education. Internet users should avoid clicking on links that point to high profile targets such as banking websites or online shopping portals. These sites may be accessed by typing the domain names manually or through the use of bookmarks on devices.
Now You: how often do you encounter phishing attacks?
Thank you for being a Ghacks reader. The post Phishing: use of reverse tunnel services to avoid detection and shutdown increases appeared first on gHacks Technology News.
